#secure proxy browser
Explore tagged Tumblr posts
Text
Fast Secure Proxy Browser: Browse Anonymously Without Limits

Have you ever tried to access a website, only to be met with a frustrating “This content is not available in your region” message? Or perhaps you've felt uneasy knowing your online activity might be tracked or exposed on public Wi-Fi. In today’s digital landscape, where privacy breaches and content restrictions are increasingly common, it’s no surprise that more users are turning to solutions that offer both security and speed.
That’s where a fast secure proxy browser comes in. It's more than just a digital detour — it’s your shield against surveillance, a bridge to open access, and a tool that puts you back in control of your browsing experience. But what exactly makes a proxy browser both fast and secure? And how can it help you browse anonymously without limits?
In this post, we’ll break down how a fast secure proxy browser works, explore why it matters, and guide you through choosing one that fits your needs. Whether you’re looking to protect your data, bypass geo-blocks, or simply surf without compromise, you’re in the right place. Let’s dive into the tools and tactics that make anonymous browsing not just possible—but effortless.
Understanding Proxy Browsers
Proxy browsers serve as intermediaries between your device and the internet. When you access a website through a proxy browser, your request is rerouted through a remote server. This server masks your IP address, effectively hiding your identity from websites, advertisers, and even government surveillance.
A proxy browser differs from a Virtual Private Network (VPN) in a few key ways. While both hide your IP and offer privacy, VPNs typically encrypt all internet traffic on your device, while proxy browsers work at the application level—usually within the browser itself. This makes proxy browsers lighter and often faster for everyday use.
Why does speed matter? Because privacy tools shouldn't slow you down. A fast proxy browser ensures you're not waiting forever for a webpage to load, all while keeping your identity secure. It also allows seamless streaming, gaming, and general browsing without buffering or lag.
With a secure proxy browser, you no longer need to worry about malicious entities tracking your every move. Your location stays hidden, your data remains encrypted, and your browsing history is safe from third parties.
Key Benefits of a Fast Secure Proxy Browser
Maintain Online Privacy and Hide Your IP
One of the biggest advantages of a fast secure proxy browser is the ability to mask your real IP address. By doing so, your digital footprint is hidden, and your activities can't easily be traced back to you.
Bypass Geo-Restrictions and Censorship
Tired of running into blocked websites? Proxy browsers help you bypass content restrictions imposed by governments, schools, or workplaces. Whether you're accessing streaming services, social media, or news outlets, you can do so freely.
Enjoy Fast Speeds Without Compromising Security
Many users avoid privacy tools due to slow speeds. Fast secure proxy browsers, however, use optimized routing and load-balancing techniques to ensure swift connections, even under heavy traffic.
Protect Data on Public Wi-Fi Networks
Public Wi-Fi is notorious for being a security risk. With a secure proxy browser, you can encrypt your traffic and ensure your data isn’t intercepted by hackers, snoopers, or malicious hotspots.
Essential Features to Look for in a Proxy Browser
End-to-End Encryption Capabilities
Ensure that the proxy browser you choose offers end-to-end encryption. This prevents any third party, including your ISP, from reading your data.
Zero-Log and No Tracking Policies
A true privacy-focused proxy browser won’t log your activity. Check for providers that openly commit to zero-log policies.
Multiple Server Locations for Flexibility
The more server locations available, the easier it is to access global content. It also allows you to switch locations if one is underperforming.
One-Click Access and User-Friendly Interface
Ease of use matters. Look for browsers that require no technical expertise and offer clean, intuitive dashboards for users of all levels.
Use Cases: Who Needs a Fast Secure Proxy Browser?
Journalists and Researchers in Restricted Regions
For those working in countries with limited internet freedom, proxy browsers offer a vital tool for uncensored information gathering.
Everyday Users Who Value Privacy
Even if you're not a whistleblower or journalist, your data matters. Proxy browsers help safeguard everyday browsing activities.
Students Accessing Blocked Educational Resources
Educational institutions sometimes block certain sites. Proxy browsers can help students bypass these restrictions to access learning materials.
Travelers Looking to Avoid Regional Content Blocks
Traveling abroad and can’t access your favorite streaming service? A proxy browser can make it seem like you're back home, unblocking content seamlessly.
How to Get Started with a Secure Proxy Browser
Choosing the Right Tool for Your Needs
Not all proxy browsers are created equal. Look for one that balances speed, privacy, and usability based on your unique needs.
Step-by-Step Setup and Configuration
Download the proxy browser from the official website.
Install and launch the application.
Select a server or location you want to browse from.
Enable encryption settings if available.
Start browsing anonymously.
Tips for Maximizing Speed and Performance
Choose servers closer to your actual location.
Avoid peak usage times when servers may be overloaded.
Clear your browser cache regularly.
Common Mistakes to Avoid
Using free proxies with poor security protocols
Forgetting to turn on encryption settings
Overlooking privacy policies and logging practices
Conclusion
In a world where digital privacy is increasingly under threat, a fast secure proxy browser isn't just a luxury—it's a necessity. From hiding your IP address to bypassing global content barriers, it empowers you to browse anonymously, safely, and without limits.
Whether you're a professional navigating sensitive research or a casual user who values their online freedom, the right proxy browser can redefine your web experience. Choose wisely, stay informed, and take control of your digital journey. Your path to a freer, more secure internet starts now.
FAQ’s
1. What makes a proxy browser fast and secure?It combines optimized server infrastructure with encryption protocols and minimal data logging, ensuring high-speed access and strong privacy.
2. Are proxy browsers legal to use?Yes, using a proxy browser is legal in most countries. However, it's important to comply with local laws regarding internet usage.
3. Can a proxy browser replace a VPN?For basic privacy and unblocking content, yes. But for full-device encryption and enhanced security, a VPN may still be preferable.
4. Do proxy browsers work on mobile devices?Many secure proxy browsers are available for Android and iOS, offering similar features as their desktop counterparts.
5. Are free proxy browsers safe? Not always. Many free services log your data or serve ads. It’s better to choose a reputable proxy browser with a transparent privacy policy.
#secure proxy browser#anonymous web browsing#bypass internet restrictions#online privacy tools#fast proxy service
0 notes
Text
I would have included this scan with my recent miscellaneous collab scans post, but I decided it deserves its own post, not just because it's one of the loveliest official Twiyor illustrations I've seen, but also because the story of how I got it is...interesting 😅

This image is from the chara fine graph (which is basically a framed picture) that was included as a preorder bonus for buying the complete season 2 blu-ray set from a shop called Rakuten Books (together with badge pins of the same designs). I briefly mentioned it back in October of last year when season 2 was airing, along with preoder bonuses from other shops like Animate and Amazon. I only wanted to get this one though, so as per my usual process of trying to secure rare SxF goods, I made a note to myself to keep an eye out for when it released. Rakuten, which I believe is the main company for Rakuten Books, has their own proxy buying service, and as the season 2 blu-rays were released, I saw them appearing there. But as noted on their main site, the condition for them to send you the chara fine graph is that you must preorder all of the three season 2 blu-ray discs from them. Once you buy the third one, if they know that you've already bought the others, then they'll send you the preorder bonuses along with it.
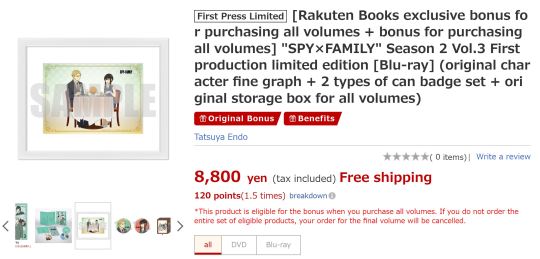
I was concerned that if I bought the discs via proxy, they wouldn't know that I bought all three and would cancel my order at the end! I would be devastated if that happened after waiting months and spending all that money on the complete set. I knew people would sell the chara fine graph second-hand as soon as it released, so I decided to wait until then and try to find it on Mercari.
So the months went by and eventually I found out that the final blu-ray volume of season 2 would release on April 17th, 2024. I made a mental note to check Mercari for it then, but unfortunately something else released around that same time...CODE: White in the US, which had its first screening on April 18th. Admittingly, I got distracted by the CODE: White release and had seen it twice by the following weekend. I did do some preliminary searching for the chara fine graph, but not with my usual refined search terms. It wasn't until the 21st that I finally sat down and really started searching for it. And while I did find a few listings, they had already been sold.
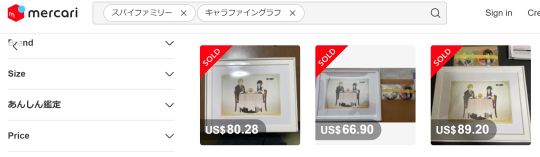
I was hopeful that more people would sell it, since it had only been less than a week since release. But I guess I underestimated how popular this chara fine graph was because, after the initial five listings I saw that were sold within the span of a few days, none appeared after. I had, like, ten Mercari tabs open on my browser with different search terms that I refreshed many times a day, but nothing was showing up. I would groan whenever I'd see the preorder bonuses for the other shops like Animate and Amazon pop up, but not Rakuten Books. I did finally see one new listing of someone selling just the badge pins, but that was sold within a few minutes, which made me even more nervous. I would also be nervous getting up in the morning since I didn't want to see that a new listing was posted and sold while I was sleeping! Thankfully I work from home so it wasn't too much of an inconvenience for me to refresh the Mercari tabs on my personal computer whenever I had a minute. But as the days went by and I didn't see any new listings, I started getting mad at myself that if I had only started seriously searching for it right on release day, I would have had at least five chances to get it and could have saved myself this hassle. I even sent a message to Rakuten Books via their online form, asking (in Japanese) if they could somehow sell it to me and ship internationally, etc. But their response was pretty much what I expected...a polite "no."
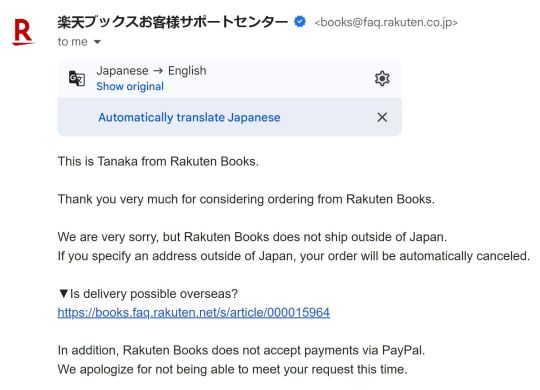
But then, on the evening of May 4th, I found a new listing and immediately bought it! What should have been a red flag though is that the person was selling it for $30 (with the badge pins included), while everyone else had been selling it from around $80-$100. The title they gave to the item was weird too; they simply called it "Spy Family" instead of "Spy Family Chara Fine Graph" or "Spy Family Rakuten Books Bonus" or something descriptive like that. But the seller had a decent rating so I didn't think there was a problem. After I got the email from Buyee (my proxy service) that they successfully bought the item, I thought I was all set. I closed out all my search tabs and went to bed feeling satisfied.
However, when I got up the next morning, my heart sank when I saw that about an hour after I had gone to bed, Buyee sent me another email saying that they refunded and cancelled my order! The reason they gave was "due to the convenience of the seller" 😫
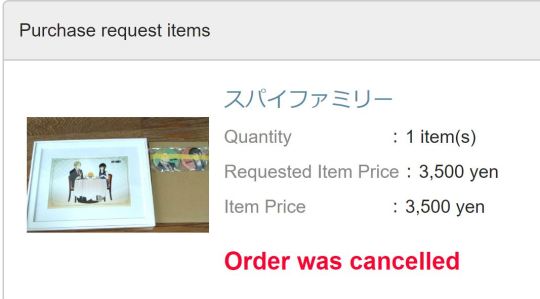
But what was most frustrating about this is that, when I checked the searches again, I saw that the same seller had relisted the item, with a higher price and more descriptive title, and it had been sold already. What probably happened is that the seller realized they made a mistake with the title and price of the listing and wanted to change it, which Mercari apparently allows them to do even after it had already been sold and paid for!
I was furious with Mercari for allowing this. The least they could do in a situation like this is give the original buyer, like, one day to buy the item again with the increased price before the seller is allowed to relist it again. I wanted to write to the seller and/or Mercari, but I wasn't able to make a Mercari account since it's restricted to Japan. I was also internally yelling at myself that if I had just started searching for it within a day or two of release instead of procrastinating, I could have avoided all this. So it was back to square one, but I wasn't going to give up! I opened up more search tabs with even more refined search terms. I also expanded to other proxy-supported shops like Surugaya and Yahoo Japan Auction. I even got my mom to help me, since she's often up in the middle of the night and can check in case anything is listed during that time while I'm asleep. I downloaded the Buyee app too so I could check listings even if I was away from my computer. With all this, I was hopeful I'd be able to buy it again, though it was more of a question of "when" than "if." With second-hand collectibles, you never know when they could pop up...I could find a new listing the next day, or not for a year or two. But I just kept up the searching, and finally, after another month went by, on June 3rd (June 4th in Japan, so technically Twiyor day 😁) I finally found it again...on Yahoo Japan Auction of all places!
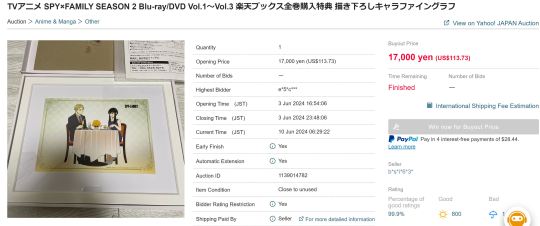
I had never bought via auction before so I was a bit nervous I'd get outbid or something. But I immediately clicked the "pay buyout price option" (which was only a few dollars more than the original price) and, thankfully, a short while later Buyee informed me that I successfully won the auction! But after what happened before, I was still paranoid that it could get canceled for whatever reason. But that didn't happen, and after waiting for shipping, it finally came~

I always like to add a "lessons learned" in these situations, so I'd say the lesson here is don't be blasé or procrastinate when it comes to something you really want. And of course, being persistent pays off more than not!
116 notes
·
View notes
Text
Why is Cloudflare blocking me?
Cloudflare is a content delivery network (CDN) and security service that helps protect websites from various threats, such as DDoS attacks, malicious bots, and hackers. If Cloudflare is blocking you, it’s likely because the security settings on the website you’re trying to access have identified your connection as potentially suspicious or harmful. Some common reasons for Cloudflare blocking your access include:
IP reputation: Cloudflare maintains a list of IP addresses known for spam, hacking attempts, or other malicious activities. If your IP address is on this list or has a poor reputation, you may be blocked.
High security settings: The website owner might have set their Cloudflare security settings to a high level, causing more aggressive filtering of incoming traffic. In such cases, even legitimate users might be blocked or challenged.
Rate limiting: Cloudflare can block or limit access from IP addresses that make too many requests within a short period, as this can indicate a DDoS attack or automated scraping attempts.
Browser or user agent issues: Using an outdated browser, a non-standard user agent, or having disabled cookies and JavaScript might trigger Cloudflare’s security measures.
VPN or proxy usage: Using VPNs, proxies, or Tor can sometimes cause Cloudflare to flag your connection as suspicious, as these tools are often used to hide malicious activities.
Firewall rules: The website owner may have set specific firewall rules in Cloudflare that block certain IP addresses, countries, or user agents.
To resolve the issue, you can try the following:
Clear your browser cache and cookies, and ensure JavaScript is enabled.
Update your browser to the latest version or try using a different browser.
Temporarily disable your VPN or proxy, if you are using one.
Check your internet connection and restart your modem or router to obtain a new IP address.
If you suspect your IP address has been mistakenly flagged, you can contact the website owner or Cloudflare support to request a review of your IP address.
Remember that these measures are in place to protect websites and their users from security threats. While blocking can be frustrating, the intent is to maintain a safe online environment for everyone.
Source @ao3org
103 notes
·
View notes
Text
https://github.com/dexter-proxy
<3
ERR_ECH_FALLBACK_CERTIFICATE_INVALID
this was my github account when I use to be really into programming , I was really good at it . Infact I was so good at it that everyone I once knew became trapped in a mixed matrix loop glitch of an 80's high-school drama flick & a super hero movie . Under ideals between war in a loop where there are no friends and where there is nothing but meaningless bitcoin . I stopped programming because after awhile I got sick of the same looped behavior in the same states of mind without really paying attention :: the loop always goes something like this [ I'm important & needed , am I villain, what good am I ] the entire ideal trying to hide the idea that I'm only lied to through fear . The idea that rape has been hunted down for a long time on the internet due to the darkwebs popularity was always something I was good at , in fact I was so good at it people made me out as a lieing joke and put my entire life on a zoo display like a child to make fun of calling it nobility . This is cursed by the old gods . Though 🤔 .... the same loop always follows because that's only the human behavior aspect that's how c++⁹⁸ was created as a subjective of C programming . Though even the idea of helping me was used against people to make people into basically brain dead nothingness hoping to hide . Sorry ( not really ) it's not my war in the first place . English is kind of lame . I made such a HUGE COOL internet trench that no one will ever explore . That's okay .
英•語目がクチる ° 本の方が使いい • 但只能在同一个循环中 ° 最终每个人都会停下来,然后这个循环再次开始 ,
that is impossible I guess to comprehend . So I made a place where we could post hentai and porn and not be bothered this
http://blueponyfdt5emnvtabzgfy36bwakan225x4fxvttgt2ov2dbkcqgdad.onion
This is my friend ^-^ ^-^ <3
error in E explorer indicates an issue with Encrypted Client Hello (ECH) and its fallback mechanism, specifically when a reverse proxy or other network middlebox interferes with the ECH handshake. This error usually occurs when a site uses ECH for secure connections, but the browser (E explorer , in this case) detects that the fallback certificate presented by the server is invalid or untrusted.
3 notes
·
View notes
Text
192.168.1.250 Netgear Setup: A Beginner’s Guide
The netgear extenders are widely used by many of the networking users to create a reliable network. Netgear extender devices are known for their performance and stable network. Setting up the extender device is not a daunting task if you are aware of the setup process. In this article we are going to elaborate in detail how you can perform 192.168.1.250 Netgear Setup using the web. Web based setup method is the most reliable way to add the netgear extender into your existing network. Gather the important details and configure any model of netgear wireless range extender device. Scroll up the page and read the information till the last to boost up your network.
Unboxing The Extender
Unboxing the wireless range extender is the first step of the 192.168.1.250 Netgear Setup. In the box you will find an extender along with power adapter, user guide and ethernet cable (optional). You need all such items for the setup process. In addition to these items you also need host router network details, working internet connection, electric power socket, and computer/ laptop device.
Placement
Second step is placement of the device. Proxy placement is needed for the setup. Put the device closer as possible. Also there is no signal interface closer to the router & extender device.
Boot Up
Next step of the process is boot up. For booting up you have to use the power adapter you got with the extender. In case your device is a wall plug compact design device then you have to directly connect it with a wall outlet. Boot process might take around 1 to 2 minutes. Before proceeding further towards 192.168.1.250 Netgear Setup using the web, wait for LED lights to stabilize.
Connect To Extender Network
Step ahead and connect the extender device to the client device using any of the given methods:
Ethernet: Use the ethernet cord you got with the range extender and connect the extender with the client device. Inject the cord’s one end into the ethernet port of the extender and other in the client device ethernet port. Make sure the connection is secured.
Wireless: Using the wireless network of ethernet you can establish a connection. Check out the device label to know the default SSID & password. Use your client device and run a scan for available wireless networks. Enter the details and connect the devices.
Access 192.168.1.250 Netgear Setup Page
Now you have to access 192.160.1.250 netgear setup page by follow the given steps:
Launch google chrome or any other similar browser.
Thereafter, mention 192.168.1.250 IP in the URL bar.
A new page appears where you have to provide default information.
Enter admin and password in the fields.
Further press login and netgear installation assistant will guide you.
Configure Extender
Once you get access to the configuration page, choose the language first and then your router’s network name. Choose next and enter the password on the screen. Further click on connect option and then next.
Secure Network
Now you have to secure the wireless network by creating an SSID & password for your extender network. Also make changes in the admin account user details. This step is important to keep your existing network secure.
Update Firmware
Afterwards, you need to look for the firmware version. In case the firmware is outdated then you should install the latest version. For installation you can opt for an online update option and follow the prompts. You can update the firmware manually also by downloading it from the official portal of netgear.
Finalize Setup
Finalize the setup by choosing the submit button once you made all the important changes in the network. Review the changes you made to verify every step. Note down the extender security details you have created and keep them secure. Submit the changes and then you can step further to reposition the device.
Reposition The Extender
Repositioning the extender is a very important step to optimize the network performance. Unplug the extender from the proxy position. Search for a midway position (from the router and the area where the dead spot was). Then plug it in again to the power at the new position. Wait for the device to boot up and monitor the router LED on your extender device. If it’s green then the position is perfect. On the contrary if it turns amber or red then relocate it.
Test New Network
Lastly, test the new network using a wireless handset. Using the new SSID & password connect the device with the extender network and browse, stream or play online to check speed.
Conclusion
Lastly, I would like to rest my words by saying that the 192.168.1.250 Netgear Setup process is a super easy task. By following the above mentioned step by step breakdown of the extender setup process, anyone can configure the extender easily without a tech expert. Setting up an extender device will boost your existing network signal strength and terminate the dead spots from your home or office area.
2 notes
·
View notes
Note
Also you mentioned a VPN, but are there any free ones? Specifically like a Firefox extension or something like that? I can't pay money for one, and i'm gonna switch to Firefox soon anyways (long story). Also ik I said this before but thx for the kitties :D
I'm not very knowledgeable on PC VPNs but I found this article linking some
What you've got to be aware is that if they're free they're always gonna have limitations.
For your phone I'm only knowledgeable on Android. Opera has a built in limited VPN. It works only on the Opera browser though.
However I've found an app that basically works as a VPN for your whole phone
It's limited in servers and I recommend you keep checking the VPN symbol from time to time as after a while it automatically turns off the VPN I think but it works for all apps that use your location which is really good.
I went looking and found this one that has a bunch more server options
It can have very long ads but that's the price for being free. Using it right now and it works 👍
I've now also tried this third option
At first it may appear like it has more options than the last one but don't be fooled! Most of the servers are premium. It does have better options if you want your location to be the US or Canada but that's mostly it. The Super Unlimited Proxy is better for European server options.
Well that's what I found for free! I hope it helps even if I know it's probable that you have an Apple device instead of Android because that's the US norm. —_—
#ask#Anonymous#VPN#Resources#Also no worries!#Don't be embarrassed by your ask#We all feel down sometimes and it wasn't something bad to vent#I don't feel burdened by your ask. I quite enjoy trying to help people.
52 notes
·
View notes
Text
Burp Suite
This week I wanted to cover a powerful tool that assists in web application security. Burp Suite is a well-known tool developed by PortSwigger. Burp Suite is an integrated platform used to test web application security by using a variety of different features it provides. One of these features Burp Suite has is an intercepting proxy that allows you to inspect and modify traffic between the browser and the server at each step. Scanner allows you to automatically detect certain vulnerabilities like SQL injection and cross-site scripting. Intruder automates custom attacks to test certain security parameters, generally passwords. Repeater allows for manual modification and replaying of edited requests for more in-depth testing.
All in all Burp Suite provides a simplified way and process for identifying and discovering vulnerabilities. It has a very user-friendly interface that assists in applying all the different features and makes it easy to learn. It also allows for user consummation that allows users to create custom rules and integrate third-party extensions. It is one of the most renowned tools in cyber security and brings an active and engaging community along with it. Burp Suite I is something I highly recommend to those striving to develop their cyber security skills to get their hands on. Not only will you become more proficient in the tool itself, but it will also teach you about how web applications and servers work.
Source:
2 notes
·
View notes
Note
how are you downloading Ici tout commence?
From the official site!
First, I use a VPN to get a French IP (or Belgian--I'm not sure which they accept, I just know these two work) so I can access the network's streaming site, TF1+. You should be able to sign up for a free account without issue. This is the page for the season 4 eps:
https://www.tf1.fr/tf1/ici-tout-commence/videos/saison-4
Apparently there are always two eps in advance available for the premium subscribers but I'm not caught up plus I think it'd be a little harder to sign up for an actual paid account so I probably won't be able to do that.
So normally I would use youtube-dl/yt-dlp to download the eps but that won't work here, or at least not without some extra steps, because these are DRMed. This is where it gets a little tricky and the whole process isn't super well documented both because it changes a lot and it makes more sense to teach people to learn how to do it than how to do it and also because, well, the more these methods are spread, the more networks change things up and make things harder.
This thread can help you get started: https://forum.videohelp.com/threads/412113-MYTF1-Help-needed-New-DRM-system-can-t-download
The whole forum is quite useful and I've only had to post for help a couple of times, mostly I just search my issue and read through.
That provided command in the second post, that's something to be used in your command line, on Windows in Start you can open that by typing in cmd or PowerShell or just google what you'll need for your computer.
These are the things you'll need to get to run the command:
N_m3u8DL-RE is a tool you can google and download, and also ffmpeg and mp4decrypt. You'll want them in the same folder for convenience. (I think you might need to install python too? If it says you do, then go ahead, lol.)
The way to get the key, this is the most gatekept part, probably. The various streamers out there use different methods of encryption and increasing security levels, and if you read up on it, you'll see stuff about kid and pssh and cdm and L3, it can be overwhelming, but in this case, the things you need are relatively easily accessible.
I'll tell you how to get the pssh and the license URL and you'll be able to use those to get the key. There are several tools you can use them on, one is public and easy, one is private but still easy-ish, and one is pretty complex and not a route I've gone down myself yet (it's the pinned thread in that particular forum). I don't want to link any of them myself, but I'll link to a thread that mentions the easy public one. It does go down at times which is why the hardcore people recommend that last method.
First, before you click on an ep, open up your browser's Developer Tools, usually Ctrl+Shift+i will do the trick. Go over to your Network tab, this shows all the requests your browser makes when you go to a site.
Then click on the episode in the actual browser. You'll see a flood of requests in the Network tab, filter on mpd.
Select the mpd result and the details for it show on the side, click on Preview. Scroll down until you see <!-- Widevine -->. A couple of lines below it, you'll see something like <cenc:pssh>AAA[a bunch of characters]</cenc:pssh>
Grab that whoooole part that starts with AAA, that's the pssh. Go to the Headers detail tab while you're there and grab the Request URL, this is the mpd link we're going to use later.
Now to get the license. Usually you can filter in your Devtools Network tab on license or, in this case, widevine. Since we're already on the Headers detail tab, grab this Request URL now, it should start with https://widevine-proxy-m.prod.p.tf1.fr/proxy?
Now go back to that easy public tool linked in that thread I linked, lol, and just fill in the PSSH and the License. Hit Send and you get a list of three keys at the bottom. I've always gone for the one in the middle and not bothered with all three, but you can try them all.
So at this point, you should be able to fully create and use the command in the first forum link above. If you read the documentation for N_m3u8DL-RE, there are various flags you can use, --save-name "Outputname" will let you name the output what you want, -sv best defaults to the best video quality, -sa best is best audio quality, and so on.
The way to get the subtitle is to turn on subtitles on the video player on the site and to go back to the DevTools box and filter on textstream. Grab the first request, the one that ends with =1000.dash and paste it into a new browser address, and change the .dash to .vtt. That's the subtitle. :) You can use the free tool Subtitle Edit to both convert it to srt, which will let most video players play it with your video, and there's also an Auto-translate option that lets you translate to English. It offers several ways but as I don't have a Google API, I just use the normal "slow" method, it's not that bad.
A second way to get the subtitle is to use the same command as when you're downloading the ep but remove the -M format=mp4 at the end, and instead add -ss 'id="textstream_fra=1000":for=all'
This was all figured out through a LOT of trial and error on my part so please do try your own best if you hit some issues, that's the best way to learn. Also, I just don't want to be the helpdesk on this, lol.
#replies#Anonymous#sent on 20240213#whew#that's a lot#but for real unless there's a huge error in what I've said just try to troubleshoot your issues on your own :x#there seems to be increased interest in this show...I wish I was in the mood to catch up#unfortch I've stopped on both this and neighbours for now...#I don't want to waste them on the mood I'm in these days#ici tout commence
17 notes
·
View notes
Text
How To Set Up Socks5 Proxy List in Wingate.me?
What Is Private Proxy Wingate.me?

Wingate.me is a private proxy service that delivers secure managed internet access across your entire network and all your online activities. It caters to a range of requirements, from small networks to large enterprises. Known for its high-quality private proxies, particularly in the Russian region, Wingate.me has carved a niche for itself as a powerful online platform.
Supporting for Internet hosting ensures that the WinGate Proxy Server is compatible with all browsers, SSL, FTP, streaming audio and video, DirectPlay Internet gaming, etc. Socks5 proxy list wingate.me provides clients with a safe, anonymous, and unrestricted internet browsing experience. They shield users from data collection and facilitate access to otherwise blocked websites.
Types of Private Proxy Wingate.me
It offers a variety of private proxy types, including:
1. SOCKS4 proxy
A versatile proxy for web browsing, file sharing and online gaming, known for its speed and efficiency.
2. SOCKS5 proxy
These proxies support TCP and UDP traffic, making them ideal for online streaming, torrenting, and high-performance tasks.
3. IPv4 proxy
Stable and reliable proxy based on IPv4 protocol, compatible with most websites and services on the Internet.
4. Mix of SOCKS5 and IPv4 proxies
This option combines the advantages of both proxy types, providing flexibility for different tasks.
An Overview Of Wingate.me’s Socks5 Proxy List
Socks5 proxy list wingate.me provides an extensive list of Socks5 proxy servers, ensuring users have access to a broad range of functional and efficient proxies. The list, updated regularly, includes information such as the IP address, port number, country, and the last time the proxy was checked for functionality. This transparency empowers users to make informed decisions when selecting a proxy server.
Get 1GB Proxy Free Trial of Residential Proxies Now!
How To Set Up Wingate.me’s Socks5 Proxy?
Setting up a Socks5 proxy from Wingate.me is straightforward. After selecting a proxy from the list, users can configure their web browsers or applications to use the proxy by entering the provided IP address and port number in the relevant settings. Specific setup instructions may vary depending on the application or browser used. Here are detailed instructions:
Step 1 Installing Wingate Proxy Server
After downloading the latest package of WinGate Proxy Server, double-click its ‘.exe’ package to start the installation setup wizard of WinGate proxy server. After that, you will be greeted by its welcome page to get started with the installation on your devices. Click on the “Next” button to continue.
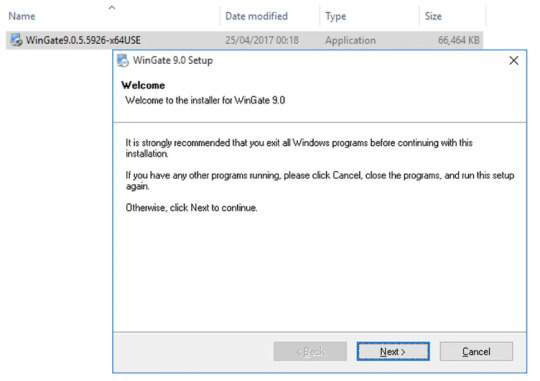
Get 1GB Proxy Free Trial of Residential Proxies Now!
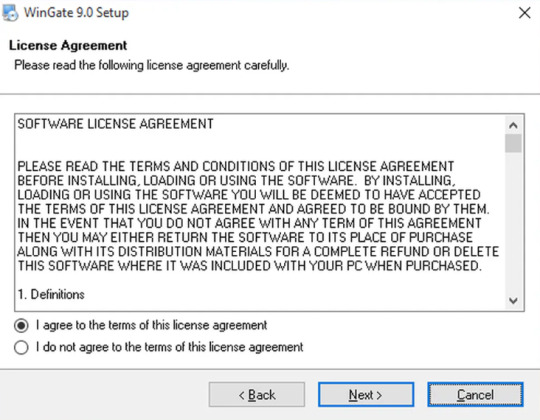
Step 2 License Agreement
You need to read and accept the license agreement before the installation and use of Wingate by choosing the right option as shown.
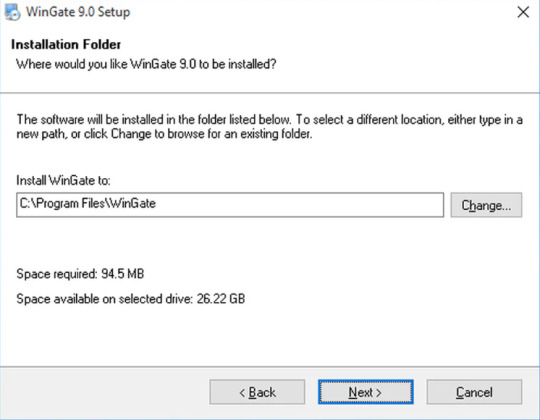
Step 3 Installation Folder
Choose the location on your system, where you like to place the WinGate installation setup.
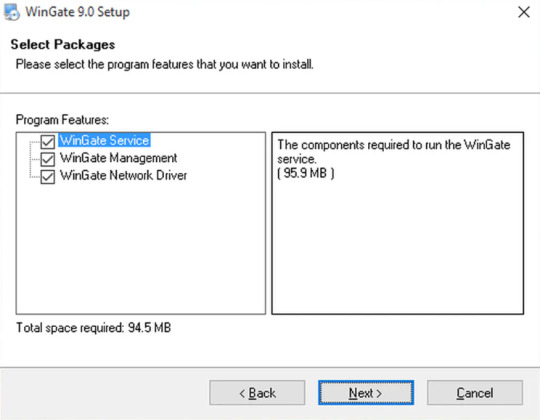
Step 4 Select Packages
You will be asked to choose the program features that you wish to install on your system.
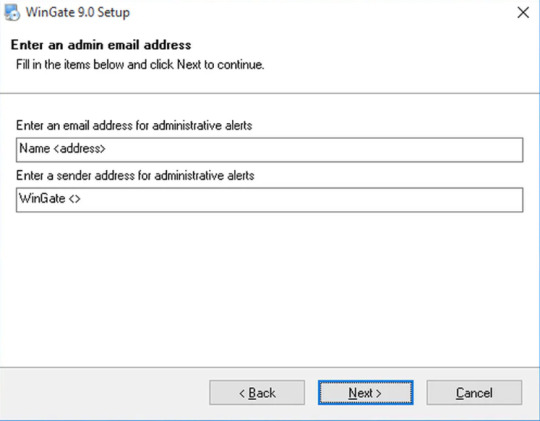
Step 5 Admin Email Address
You should provide your Administrative User Name and Email ID along with the Senders’ address for the administrative alerts.
Step 6 Ready to Install
If you click on the ‘Next’ button, your installation process will start processing files and other selecting configurations. After finishing the installation process of WinGate, click on the ‘Finish’ to exit the installer. Remember to click on the ‘Yes’ to go for system reboot and wait till it is back.

Step 7 Setting Up
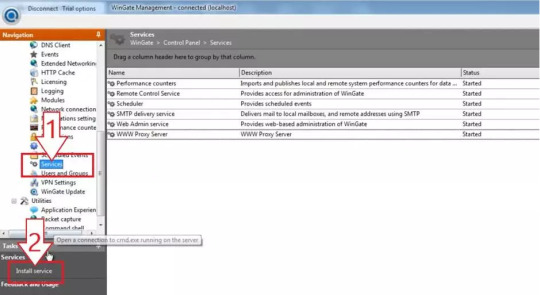
After you finish the installation, you can set up Wingate.me’s Socks5 Proxy List now.
1. You will see a welcome page and a navigation menu on the left with available configuration options. Please focus on setting up the proxy. To do this, select “Services” from the navigation menu, then right-click on the empty space on the right and select Install Service.
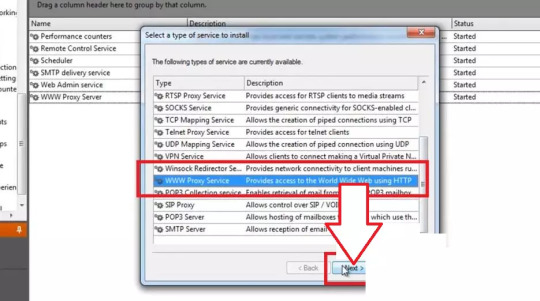
2. The service properties window will appear. Navigate to the Bindings tab. Remove all active bindings and click Add. Select “Any External Adapter” and click “OK” to save your configuration.
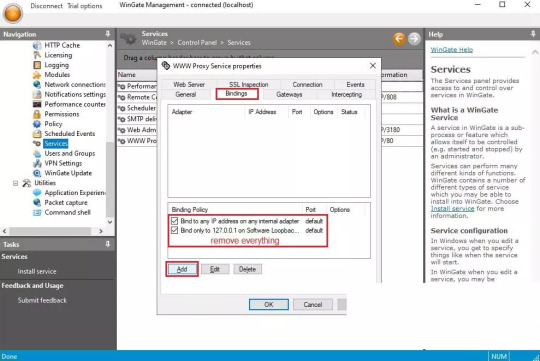
3. Now, go to the Connection tab. Check the box next to “Connect through upstream proxy.” Go to the IP Settings dashboard to configure your proxy. Note down the HTTP proxy host, proxy port, proxy username and proxy password of the private proxy you obtained from the website and import this data into WinGate.

By following these steps, you will successfully configure a private proxy using Wingate’s user-friendly interface. This ensures safe, anonymous and efficient internet browsing while protecting your online activity and data.
Get 1GB Proxy Free Trial of Residential Proxies Now!
Conclusion
Wingate.me’s Socks5 proxy list is a powerful tool for anyone seeking to navigate the digital world with anonymity, versatility, and global access. However, like any tool, it should be used responsibly and ethically. As we continue to sail through the data-driven era, tools like Wingate.me’s Socks5 proxy list will undoubtedly play a crucial role in shaping our digital experiences.
For more please read the original article which is from:
#socks5 proxy list wingate.me
#private proxy wingate.me
#buy wingate me private proxy
#proxy for email wingate.me
3 notes
·
View notes
Text
Smiling softly to himself as he watched his friend , and travel companion busy herself by starting to affectionately play with Lady Asta's pet dog , he figured that with their most recent stop here to Lady Herta's Space Station that he'd have some free time to catch up on some personal affairs .
Leaving , knowing full well that he could leave March 7th in the capable hands of Lady Asta , Arlan , and the Trailblazer themselves he wouldn't go out too far . Though they weren't due to leave anytime soon . Traveling by himself to an area of the space station where he could find some solace , and privacy to get some work in .
Well ... as much privacy as one could find when Lady Herta had eyes and ears built in quite literally everywhere on her ship .
Reaching into his pockets , once he'd manage to find a computer terminal to work off of , he'd insert a thumb drive into the machine . Folding his hands over his chest as he watched the computer perform the necessary security measures of scanning his drive for any malware , then just as quickly downloading all the files that he'd amass within it thus far . Copying them into a specified series of folders .
It was nothing extraordinary , just a few minor research projects that he'd been tasked with completing by staff from the station . Projects that were never a requirement of him remaining both a traveler , and a trailblazer aboard the Astral Express but rather commissions that had been posted offering money in exchange for completion . Simple things .
In his earliest days of trailblazing it had been a bit embarrassing to have to rely on others for income so this had been a means of earning his own money to avoid any future awkward situations and pay back those he owed .
A vibration coming from his phone resting in his pockets would soon confirm the successful transfer of credits into his personal bank accounts .

With that done , Dan would eject his thumb drive from the computer , and open up a few tabs on his web browser to see if there were any more projects he could take on in the meantime . Aside from being a means of earning some credits here and there ... it was also a means of keeping busy , and learning more about the Universe he was helping to explore through hands on research . It was always interesting ... and maybe a bit fun for him too .
As chat messages began to pop up on his sidebars , he was lucky to be in the position of a traveler when undertaking these projects . He could obtain materials or document phenomenon that most researchers would either have to go out themselves to get , or pay hefty sums of their allocated budgets to hire outside help .
Truth be told , he was starting to suspect that some of his benefactors might have been the lead researcher of the station Lady Asta herself speaking through proxies or false accounts . Regardless , the pay was still good so he didn't mind .
Sliding his gloved fingers across from one screen to the next , it was best to only accept research projects that if required , would most likely be in close proximity to where their next destination would be as he certainly wasn't going to ask to make alterations to the Express's schedule . That was out of the question for him .
Thumbing his way through different project descriptions , some were accepted with a simple affirming click , others dismissed with a casual wave . With each acceptance , his terms of service would automatically be sent out to the job posters to ensure that they understood how he worked . He had a feeling that he would soon be dispatched on another trail blazing expedition in the near future with the Trail Blazer , March 7th , and another new passenger .
With the Trail Blazer , and another new passenger set to join them he could only guess that Lady Himeko might try to send them all together out on the next expedition . Best not to take anything that had a pending deadline .
With that done , his next task would be to go through the station's virtual library to start picking out and choosing what research reports , guides , and references he would need to help him work through the current listing of projects he'd picked out for himself ...
With time passing him by as his mind focused solely on reading the electronic documents before him , he'd no sooner finish placing an order for some actual physical books to be delivered onboard to the express before departure that his cellphone suddenly began vibrating a few more times in quick succession in his pocket . He could only guess , March 7th .
Fishing his phone out of his pocket , and glancing at the lock screen to see pending message notification from their group chat awaiting his response . He'd soon rise , unlock his phone to type out quick responses , and would soon be on his way back towards the express to help with the both boarding process of loading on supplies as well as to properly greet their newest addition .
@capravulpes
4 notes
·
View notes
Text

Fire VPN-Secure Your Digital life
A Fire VPN-Virtual Private Network, is a secure technology that encrypts your internet connection, protecting your data from unauthorised access. It masks your IP address and location, ensuring online privacy. Fire VPN enables you to bypass geo-restrictions and access blocked content. They are especially useful on public Wi-Fi networks, safeguarding your sensitive information. While VPN provides added security, it's crucial to remember they don't make you entirely anonymous. To maximise protection, maintain strong passwords, keep devices updated, and remain cautious online.Fire VPN offer privacy, security, and freedom by creating a secure tunnel between your device and the internet.
2 notes
·
View notes
Text
How Static ISP Proxies Help You Avoid CAPTCHA and Bans by Proxy Lust, Inc.
In the age of intelligent bot detection and hyper-vigilant web security, getting past CAPTCHA screens and IP bans is more challenging than ever. Businesses, marketers, and automation specialists are constantly battling access blocks and rate limits, especially when using traditional proxies.
Enter Static ISP Proxies—the sweet spot between residential authenticity and datacenter performance.
In this blog post, we’ll explore what static ISP proxies are, why they’re so powerful, and how they help you avoid CAPTCHA triggers, bans, and blocks.
🌐 What Are Static ISP Proxies?
Static ISP Proxies are IP addresses assigned by real Internet Service Providers (ISPs), hosted on powerful datacenter infrastructure. Unlike traditional datacenter IPs, which are often flagged due to known ranges, static ISP proxies appear as real residential connections to websites—but with the reliability and speed of datacenter networks.
Key characteristics:
IPs registered to real ISPs (e.g., Comcast, AT&T, Verizon)
Hosted on physical servers with high uptime
Assigned a static (non-rotating) IP address
Geolocated like typical home user connections
🛡️ Why CAPTCHA and Bans Happen
Websites and platforms use anti-bot technologies to protect themselves from abuse. These systems analyze patterns like:
Too many requests from a single IP
Use of known proxy/datacenter IPs
Repetitive or scripted actions
Inconsistent browser fingerprints
If a system suspects a bot or scraper, it will:
Present a CAPTCHA challenge
Trigger rate limiting
Temporarily or permanently ban the IP address
✅ How Static ISP Proxies Help You Stay Under the Radar
1. Residential Trust, Datacenter Stability
Because static ISP proxies are tied to real ISPs, they look like residential traffic, which reduces suspicion from web services. But unlike real residential proxies, they are always online, faster, and more reliable.
2. Avoid Triggering Anti-Bot Systems
Static ISP proxies don’t rotate like mobile or residential proxies, which means no IP jumping. This reduces fingerprint inconsistency and makes your requests look more natural to the target website.
3. Bypass CAPTCHA Screens
CAPTCHA triggers are often linked to:
Datacenter IPs
High activity from one source
Suspicious browser behavior
Static ISP proxies eliminate the first issue and can be paired with real browser environments (e.g., Puppeteer, Selenium with stealth plugins) to solve the others.
4. Reduce Account Lockouts
For users managing multiple social media, eCommerce, or ad accounts, static ISP proxies reduce the risk of login verifications, phone number checks, or temporary bans.
5. Persistent Sessions
Unlike rotating proxies, static ISP proxies maintain a single IP throughout a session or task. This makes them perfect for:
Logging in to accounts
Running long-term bots
Interacting with platforms that rely on consistent IP fingerprints
💼 Ideal Use Cases
Use CaseWhy Static ISP Proxies Are IdealSneaker CoppingTrusted IPs avoid ban lists used by retail platformsSocial Media AutomationAppear as real users, lower risk of suspensioneCommerce & Classified PostingConsistent IPs prevent region/IP flaggingAd VerificationView ads like a regular user from a target locationWeb ScrapingFewer bans and block pages due to lower bot suspicion
🔍 Static ISP vs Datacenter Proxies
FeatureStatic ISPDatacenterTrust LevelHigh (residential-like)Low (easily flagged)SpeedFastVery fastBans & CAPTCHAsRareCommonIP RotationStaticOften rotatingBest ForAutomation, scraping, account managementBulk scraping, testing
🚀 Why Choose Proxy Lust’s Static ISP Proxies?
At Proxy Lust, Inc., we offer:
True static ISP IPs tied to Tier-1 ISPs
Dedicated IPs (not shared)
Geo-targeted availability in the U.S., Canada, and EU
High-bandwidth and low-latency connections
24/7 support for setup, troubleshooting, and performance tuning
👉 Browse Our Static ISP Proxy Plans →
Avoiding CAPTCHAs and bans isn’t just about having more IPs—it’s about having the right kind of IPs. Static ISP proxies combine the best of both worlds: the trustworthiness of residential IPs and the stability of datacenter infrastructure.
If you’re serious about automation, account management, or large-scale scraping in 2025, static ISP proxies are a game-changer.
Need help getting started? Our team at Proxy Lust is ready to help you deploy the perfect proxy solution for your project.
0 notes
Text
0 notes
Text
if you download this zip file at the internet archive, there is an .exe inside that when ran, contains the following Cartoon Network flash games. i verified this myself:
-The First Row- Ben 10 Critical Impact Ben 10 Krakken Attack Boomerang Bugs Bunny Toonamajig Boomerang Flinstones Runaround Fred Boomerang Gazoo's Guessing Gizmo Boomerang Marvin Snapshot Boomerang Memory Tooner Camp Lazlo Jumping Jelly Beans -The Second Row- Camp Lazlo Paintcan Panic Dexter Clone-A-Doodle Doo Dexter Runaway Robot Dexter Snapshot Ed Edd and Eddy Spin Stadium Ed Edd and Eddys Candy Machine Fosters Home for Imaginary Friends Wheeeee! Fosters Home for Imaginary Friends Wilts Wash N Swoosh -The Third Row- Hi Hi Puffy AmiYumi Dish it Out Johny Bravo Whuzzat KND Flight of The Hamsters KND Numbuh Generator KND Operation S.T.A.R.T.U.P KND Operation S.T.A.T KND Operation Tommy KND Tommy Trouble -The Fourth Row- My Gym Partners a Monkey Front Page Nuisance PowerPuff Girls Meat The Mayor PowerPuff Girls Snapshoot PowerPuff Girls Zom-B-Gone! Robot Boy - Tommy Takeaway Robot Boy Depth Charger Samurai Jack Code of The Samurai Scooby Doo and The Creepy Castle -The Fifth Row- Scooby Doo Swami Shaggy Scooby Snapshoot The Grim Adventures of Billy and Mandy Grims Downfall The Grim Adventures of Billy and Mandy The Fright Before Christmas The Grim Adventures of Billy and Mandy Zap To It Tom and Jerry Refriger - Riders Tom and Jerry Toms Trap-o-Matic
at the Flashpoint Archive, more than 200k additional games and flash animations have been archived as well. you can visit it here:
Flashpoint Archive is a community effort to preserve games and animations from the web. Internet history and culture is important, and the web is evolving at such a rapid pace that what might be commonplace today could be obsolete tomorrow. This project is dedicated to preserving as many experiences from these platforms as possible, so that they aren't lost to time. Since December 2017, over 200,000 games and animations have been preserved across more than a hundred browser plugins and web technologies. In addition to our preservation efforts, we also provide a highly flexible software package for reliable navigation and playback of preserved content. Among the software that powers Flashpoint is a fully-featured launcher that acts as a frontend for the collection, a proxy that tricks games into thinking they're running on the live web, and a sandbox that allows for secure playback of plugin-enabled content - all of which are open-source software.
enjoy the internet as it used to be and start archiving stuff being made today so we can hopefully enjoy it in another 20 years.
you used to be able to play games on cartoonnetwork.com . . . now every company's website wants to give you spyware and spread corporate propaganda but I REMEMBER when you could play a BEN 10 adventure game in-browser without so much as giving away your e-mail. people's heads should be on pikes for this
62K notes
·
View notes
Text
Ticketmaster Error Code U226: Causes, Fixes, and Preventive Tips
Ticketmaster is the go-to platform for millions of people purchasing event tickets—from concerts and festivals to sports and theater shows. However, encountering issues during checkout can be frustrating, especially when you're trying to secure high-demand tickets. One common and often confusing problem users report is Ticketmaster Error Code U226. If you've seen error code: U226 flash across your screen, you're not alone. In this guide, we'll break down everything you need to know about this error—why it appears, how to fix it, and how to avoid it in the future.

What Is Ticketmaster Error Code U226?
Error Code U226 is a security-related error on Ticketmaster that typically occurs when the system suspects that your activity may be automated or suspicious. It’s essentially a protective response from Ticketmaster’s fraud detection algorithms. If you encounter error code U226, it means your access to purchasing tickets has been temporarily restricted.
Why Does Error Code: U226 Occur?
The main causes of this error include:
Rapid clicking or refreshing the page
Using browser extensions or VPNs
Multiple tabs open on Ticketmaster simultaneously
Automated scripts or bot-like activity
Excessive failed login or payment attempts
Ticketmaster's system is designed to protect fans from scalpers and bots, which unfortunately means that even regular users can sometimes trigger this error.
Common Scenarios Where You Might See Error Code U226
Understanding the context in which the Ticketmaster error code U226 occurs can help you avoid it. Here are some scenarios:
1. Trying to Purchase High-Demand Tickets
When a popular event goes on sale, thousands of users flood the Ticketmaster website. In such high-traffic moments, even legitimate fans may appear suspicious to Ticketmaster’s algorithms, especially if they’re refreshing constantly.
2. Logging In From Multiple Devices
If you’re logged into Ticketmaster on your phone, laptop, and tablet all at once, you increase the risk of getting flagged for suspicious behavior.
3. Using Automation Tools
Some users attempt to use browser automation tools or bots to improve their chances of getting tickets. Ticketmaster is particularly sensitive to this and will issue error code U226 to block the activity.
4. Use of VPNs or Proxies
VPNs mask your IP address, but they can also trigger fraud protection systems. If you’re on a VPN, Ticketmaster may see it as an attempt to bypass regional or security restrictions.
How to Fix Ticketmaster Error Code U226
Fortunately, there are several ways to fix error code: U226 and get back to purchasing your tickets.
1. Stop All Activity Immediately
Once the error appears, stop refreshing, clicking, or navigating. Take a break for about 10–30 minutes to avoid prolonging the temporary block.
2. Clear Browser Cookies and Cache
Cached files and cookies can store data that triggers the same error again. Here’s how to fix it:
Go to your browser settings
Clear browsing data (cookies, cache, and history)
Close and reopen your browser
Try accessing Ticketmaster again
3. Disable Extensions and VPNs
Ad blockers, script blockers, or VPN tools can interfere with how Ticketmaster interprets your behavior. Disable all extensions and VPNs, then refresh the page.
4. Use a Different Browser or Device
Switching to a new browser (e.g., from Chrome to Firefox) or using a different device (like your smartphone instead of your laptop) may bypass the error.
5. Reset Your Network
Restart your router or use a different internet connection. Sometimes your IP address is temporarily flagged—changing it can help.
Preventing Future Error Code U226 Incidents
Avoiding the Ticketmaster error code U226 in the future requires understanding best practices for using the platform.
1. Avoid Over-Refreshing
While it’s tempting to refresh repeatedly when tickets are about to go on sale, limit your refreshes. Let the page load fully before trying again.
2. Stick to One Tab and One Device
Only use one tab and one device when trying to buy tickets. Multiple sessions from the same account are likely to be flagged.
3. Don’t Use Bots or Scripts
Ticketmaster actively fights automated ticket-buying tools. If you’re using browser automation, you will almost certainly trigger U226.
4. Stay Logged In Before the Sale
Log into your Ticketmaster account 10–15 minutes before the sale and keep your information ready (billing, payment, etc.) to speed up checkout without erratic behavior.
5. Avoid Public Wi-Fi
Public networks can make your activity look suspicious. Stick to trusted home or mobile networks.
When to Contact Ticketmaster Support
If none of the above solutions work, and you keep getting error code: U226, you may need to reach out to Ticketmaster’s customer support.
Steps to Contact Support:
Go to Ticketmaster Help
Click on "Contact Us"
Use the live chat option or request email assistance
Provide the full error message, browser used, and what you were trying to do when it occurred
Ticketmaster can sometimes manually lift a restriction, especially if it’s affecting your ability to access a time-sensitive ticket sale.
FAQs About Ticketmaster Error Code U226
Q: How long does Ticketmaster Error U226 last? A: It can last anywhere from a few minutes to a few hours depending on the activity that triggered it.
Q: Can I get banned permanently because of U226? A: No. This is typically a temporary restriction. However, repeated violations could result in longer blocks.
Q: Is there a way to know if I’ve been flagged before trying to buy tickets? A: Unfortunately, Ticketmaster does not notify you beforehand. You’ll only know if an error like U226 appears during activity.
Final Thoughts: Stay Smart to Avoid U226
Getting hit with Ticketmaster error code U226 during a hot-ticket sale is frustrating, but understanding what causes it and how to avoid it can make a big difference. The key lies in being patient, using the platform responsibly, and avoiding behavior that mimics bots or scalpers. Whether you're chasing concert tickets or seats at the next big game, keeping your Ticketmaster activity clean and human-like is the best way to stay on the right side of their security systems.
0 notes
Text
ACCA DipIFR Remote Exam: Requirement, Set-up & Tips

In our previous blog, we discussed ACCA DipIFR exam utility interface & answer writing tips which will help students to get comfortable with CBE interface and to be familiar with the examination pattern and face it with confidence.
This blog is especially for the students who chose Remote examination session i.e., who would appear from home or office instead of centre-based examination. This blog will guide you about technical requirements of the allowed devices and necessary care to be taken before and during the remote examination session.
System Requirements:
Operating System
• Windows 11 and 10 (64-bit) – (excluding ‘S Mode’) • macOS 13 and above – (excluding beta versions)
Note: • Mac OS, starting with Mojave, now requires permission from the user to allow any hardware access to an application, which includes OnVUE (proctorapp). Candidates should be prompted to allow this application • Windows Operating Systems must pass Genuine Windows Validation.
Unsupported operating systems
• Windows 8/8.1, Windows 7, Windows XP, and Windows Vista • Linux/Unix and Chrome based Operating Systems
Firewall
• Corporate firewalls should be avoided as they often cause this delivery method to fail. • VPNs and proxies should not be used. • We recommend testing on a personal computer. Work computers generally have more restrictions that may prevent successful delivery.
RAM Required
Recommended Minimum RAM of 4 GB or more
Display
Minimum Resolution: 1024 x 768 in 16-bit col Recommended Resolution: 1920 x 1080 or higher in 32-bit color • If using an external monitor, you must close your laptop and use an external keyboard, mouse, and webcam. • Multiple monitors are forbidden. • Touch screens are strictly forbidden.
Webcam
• The webcam may be internal or external. It must be forward-facing and at eye level to ensure your head and shoulders are visible within the webcam. • The webcam must remain in front of you and cannot be placed at an angle. • Webcam filters are not allowed (for example, Apple’s ‘Reactions’). • Webcam must have a minimum resolution of 640x480 @ 10 fps.
Note: • Mobile phones are strictly prohibited as a webcam for exam delivery. • Mac OS users may need to allow OnVUE within their System Preferences: Security & Privacy: Privacy settings for camera & microphone.
Speakers and microphone
Speakers: • Speakers must be built-in or wired. • Bluetooth speakers or the use of headphones* as speakers are not allowed. Headphones: • Headphones and headsets are not allowed unless explicitly approved by your test sponsor. • If allowed, headphones must be wired – Bluetooth are not allowed.
Browser settings
Internet Cookies must be enabled.
Device
All tablets are strictly prohibited, unless they have a physical keyboard and meet the operating system requirements mentioned earlier.
Power
Make sure you are connected to a power source before starting your exam to avoid draining your battery during the exam.
Internet Browser
The newest versions of Microsoft Edge, Safari, Chrome, and Firefox, for web registrations or downloading the secure browser.
Internet Connection
• For better performance, a reliable and stable connection speed of 12 Mbps download and 3 Mbps upload required. • We recommend testing on a wired network as opposed to a wireless network. • If testing from home, ask others within the household to avoid internet use during your exam session.
We strongly recommend using equipment that meets or exceeds the Recommended Specifications. The minimum requirements will change periodically based on the needs of exam sponsors.
Mobile phone: You may have the option to use your mobile phone to complete the check-in process. The mobile must meet the following requirements:
• Android (11+, Chrome) or IOS (15+, Safari) operating systems • A functioning camera with a stable internet connection
A mobile phone is used only for completing admission steps and must not be used during the exam. After completing the check-in steps, please place the mobile phone where it is not accessible to you during the exam. As a reminder, phones are a prohibited item and should not be within your reach or visible to you while sitting in front of your computer.
Pre-exam requirements
Passing the Mandatory system test
• You MUST pass mandatory system test prior to your check-in for exam. • When taking the test, use same device and the same location you we’ll use on exam day. • Make sure your last test run is a pass, so that you are eligible for all post-exam options. • Go to Exam Planner & hit the Run System Test button.
Practice using the scratch pad
Remember, you cannot use scratch paper for remote exam session. So, it’s important to get used to using the scratch pad on the Practice Platform before your live exam.
Exam set-up
Your room setup
You will be under exam conditions and monitored by an invigilator throughout. Make sure below conditions are being followed: • A private and quite room with solid walls and doors. • No other person can be visible or heard for full duration of exam. • Use curtains or blinds to cover windows if anyone can be seen through them. • Switch all other unnecessary electrical equipment off. • Refer below images to have an idea about ideal exam environment.
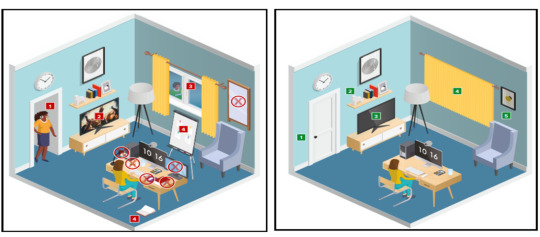
Prohibited Permitted
Your desk setup
Your desk must be setup in a way that meets the rules and regulations of the exam: • No scrap paper• Only one monitor • A glass/bottle of water with label removed permitted • No headphones / earbuds / earphones • No watches
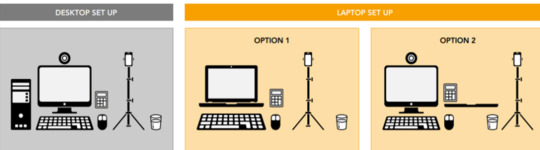
The check-in process
• Check in to your exam by going the exam planner and click launch exam button. • You can launch your exam 30 minutes prior your scheduled time. • If you are more than 15 minutes late you will miss your exam attempt and be marked as Absent.
Using your mobile phone:
• You may use your mobile phone during the check-in process – On-screen instruction will guide you.• You’ll be asked to take and upload photos of your exam environment, yourself and your ID. • Once completed this process place your mobile phone on silent and out of arm’s reach. • Do not use your mobile phone for any other purpose during exam (exception if invigilator calls you) • Taking photos of your screen or making calls during the exam is strictly prohibited.
Under exam conditions:
In addition to the desk/room requirements you should be aware that the following is also prohibited:
• Talking aloud during your exam. • People being audible outside your room. • Leaving the exam early – DO NOT end your exam early, you must stay supervised for the full-time duration.
Contacting the invigilator
• To start a chat with your invigilator, select the chat button. • Your invigilator will be with you as soon as they are available. • Unlikely they can assist you, but you should inform your invigilator if you are experiencing any technical difficulties. • You must inform your invigilator if you wish to use your permitted bathroom break.
Bathroom breaks
You can take one bathroom break during your exam of up to 5 minutes: • Notify your invigilator when you are leaving and returning from bathroom break. • You do not have to wait for the invigilator to give you their permission before taking your bathroom break. • The exam timing will continue to run – if you exceed 5 minutes your exam may be terminated.
Post-exam options: In the event of technical issue disrupting your exam, you may wish to use post-exam options which can be accessed on exam planner or under Contact Us on ACCA’s website.
Minimise the risk of the technical issue by: • Performing your equipment and connectivity test. • Accessing troubleshooting resources.
Using post exam options
To use rebook or withdrawal option you must have: • attempted to check-in your exam • experienced a technical issue impacting your ability to complete exam.
Additional withdrawal eligibility criteria
• The mandatory system test must be taken ahead of each exam session. • Student must have passed the mandatory system test in their last attempt prior to checking in for your exam.
Make sure that your device / other equipment’s are compatible as per the provided requirements and you are availed with the environment requisite for the exam purpose. Everyone should make sure to follow fair practices during exam to avoid any disqualification or disciplinary action.
We hope, this blog about ACCA DipIFR Remote Exam Requirement, Set-up & Tips shall assist in making the necessary arrangements.
Further, please watch video related to the remote examination on the below link: https://youtube.com/playlist?list=PLRYOefFr48S0apGK6f0kw0sX7fC6uSzsx&feature=shared
Best wishes from Team FinPro!
#finproconsulting#diploma in ifrs#accounting#dipifrs#ifrs#ifrs online classes#finpro consulting#dipifr course#diplomainifrs#acca
0 notes